
Table of Contents (Start)
Authentication Settings
This documentation applies to NMS version 5.4. An online version of the software can be found here.
The Authentication Settings page enables you to configure SevOne NMS to use LDAP, RADIUS, and TACACS, protocol authentication.
-
Lightweight Directory Access Protocol (LDAP) - An application protocol to query and modify directory services that run over TCP/IP to enable maintenance of centralized user directories to which distributed applications authenticate.
-
Remote Authentication Dial In User Service (RADIUS) - A network protocol that provides centralized access, authorization and accounting management for people or computers to connect and use a network service.
-
Terminal Access Controller Access-Control System (TACACS) - A remote authentication protocol that communicates with an authentication server commonly used in UNIX networks.
To access the Authentication Settings page from the navigation bar, click the Administration menu, select Access Configuration, and then select Authentication Settings.
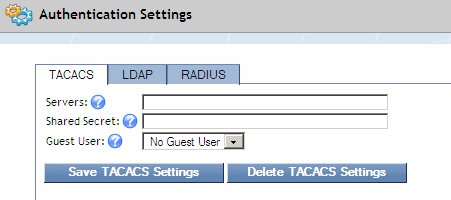
TACACS
The TACACS tab enables you to configure SevOne NMS to communicate with the TACACS protocol authentication server.
-
In the Servers field, enter a comma delimited list of the IP addresses of the TACACS authentication servers. The servers in the list are tested in the sequence in which they appear in the list. If the first server is running and the user does not have the proper credentials, then the user cannot log on. If that server is not running then the second server in the list attempts to log the user on.
-
In the Shared Secret field, enter the shared secret for the server.
-
Click the Guest User drop-down and select the user to provide permissions for anyone who logs on with a valid TACACS ID but no SevOne NMS account.
-
Click Save TACACS Settings.
LDAP
The LDAP tab enables you to configure communication with the LDAP protocol authentication server. SevOne NMS supports LDAP authentication for individual users and LDAP group synchronization for LDAP, Active Directory, and OpenSSL.
Any LDAP authenticated user that has the Must Change Password at Next Logon (or similar) setting on the LDAP server and has NOT changed said password will NOT be able to log on to SevOne NMS. Either disable this setting for the user at the LDAP server or ensure that LDAP users change their passwords elsewhere before an attempt to log on SevOne NMS.
When LDAP Group Synchronization is enabled, SevOne NMS attempts to synch LDAP users from any configured groups into the SevOne NMS user repository on an hourly basis. Relevant properties are populated per the following:
-
givenname -> First Name
-
sn -> Last Name
-
mail -> Email
Manage LDAP Servers in SevOne NMS
The LDAP Servers section enables you to configure communication with the LDAP protocol authentication server.
 - The Actions icon enables you to add and manage the LDAP servers in SevOne NMS.
- The Actions icon enables you to add and manage the LDAP servers in SevOne NMS.
-
New Server – Select to add an LDAP server to SevOne NMS.
-
Edit Server - Select to edit the LDAP server you select.
-
Test Settings - Select to test the connection to the LDAP server.
-
Delete Server - Select to delete the LDAP server you select.
Add/Edit LDAP Servers to SevOne NMS
Perform the following steps to add or edit the LDAP server settings that SevOne NMS uses to authenticate users.
-
Click
 Actions and select New Server to display the New Server pop-up. Perform the following steps to define the servers to use to authenticate using LDAP.
Actions and select New Server to display the New Server pop-up. Perform the following steps to define the servers to use to authenticate using LDAP. -
In the Server field, enter the host name or IP address of the LDAP server.
-
In the Port field, enter the network port of the LDAP server. The default LDAP port is 389. The default LDAPS port is 636 which has been deprecated.
-
In the Base DN field, enter the base distinguished name (DN) on which to do LDAP queries. The top level of the LDAP directory tree is the base, referred to as the base DN from which a search starts. For an Active Directory system this is typically dc=example, dc=com.
-
In the Bind DN field, enter the name of the user SevOne NMS is to use to authenticate to the directory. This is the username that is authorized to perform searches within the context of the Base DN in the previous step.
Example:cn=guest
-
In the Bind Password field, enter the password for the user name you enter in the previous step. This is not required in LDAP version 3 (LDAPv3).
-
In the Confirm Password field, reenter the bind password.
-
In the Username Field, enter the LDAP field SevOne NMS is to check to find user names. In Active Directory, this is typically sAMAccountName. Many other directories use cn or uid.
-
Click the Encryption drop-down.
-
Select No Encryption to not use encryption.
-
Select StartTLS to use StartTLS. StartTLS secures the LDAP credentials and data. Start TLS is sometimes referred to as the TLS upgrade operation because it upgrades a normal LDAP connection to a connection that is protected by TLS/SSL.
-
Select SSL (LDAPS, dep) to use Secure Socket Layers (SSL). SSL secures LDAP data. A method to secure LDAP communication is to use an SSL tunnel. This is denoted in LDAP URLs by using the URL scheme "ldaps". The use of LDAP over SSL was common in LDAPv2. This usage has been deprecated along with LDAPv2.
-
-
Click Save to save the LDAP server settings.
-
Repeat the New Server steps to add additional LDAP servers.
Synchronize Roles/Groups
The Synchronized Roles section enables you to associate the LDAP server groups on the LDAP server to the User Roles in SevOne NMS.
-
Click the Group drop-down and select the server group to which to associate the server you select. LDAP groups are the equivalent of SevOne NMS user roles.
-
If the group you are looking for does not appear, click Add Groups to display the Add Groups pop-up.
-
Click the Server drop-down and select a server.
-
In the Search field, enter at least one letter to filter the search results and press Enter.
-
In the list of groups, click the + next to the group name to display the group members.
-
Select the check box for each group to add.
-
Click Add to add the groups you select.
Preferences
The Preferences section enables you to define the guest user and to manage the LDAP certificates.
-
Click the Guest User drop-down and select the guest user to provide permissions for anyone who logs on with a valid LDAP ID but no SevOne NMS account.
-
Next to the SSL/TLS Certificates caption, click Upload New to display the Upload SSL/TLS CA Root Certificates pop-up. You must upload the CA Root Certificates to enable SevOne NMS to communicate with an LDAP server that has certificates that are signed by an unknown CA.
-
Click Browse to locate and select the certificate. The certificates must be base64-encoded PEM files.
-
Click Upload to upload the certificate.
-
Select the Ignore SSL/TLS Certificates check box to skip verification of the server (not recommended).
-
Click Save LDAP Settings.
RADIUS
The RADIUS tab enables you to configure SevOne NMS to communicate with the RADIUS protocol authentication server.
-
Click Add New to display the Server Settings pop-up.
-
In the IP Address field, enter the IP address for the RADIUS server.
-
In the Port field, enter the RADIUS sever port number.
-
In the Shared Secret field, enter the RADIUS server shared secret.
-
Click Save to save the server settings.
-
-
Repeat the Add New server setting steps to add additional RADIUS servers.
-
Click the Encryption drop-down and select the type of encryption to use.
-
Click the Guest User drop-down and select the guest user to provide permissions for anyone who logs on with a valid RADIUS ID but no SevOne NMS account.
-
In the RADIUS NAS Identifier field, enter the RADIUS NAS identifier, if required (default - local host if left blank).
-
In the RADIUS Calling Station ID field, enter the RADIUS calling station identifier, if required (default - 127.0.0.1 if left blank).
-
Click Save RADIUS Settings.