
Table of Contents (Start)
User Role Manager
This documentation applies to NMS version 5.4. An online version of the software can be found here.
The User Role Manager enables you to define the permissions, device/device group/device type access, and user/user role access that enables you to restrict what users can do and see in the application. User roles are hierarchical. Each lower level (child) user role can have either the same permissions as its parent user role or a subset of the permissions of its parent user role. You can assign users to multiple roles.
To access the User Role Manager from the navigation bar, click the Administration menu, select Access Configuration, and then select User Role Manager.
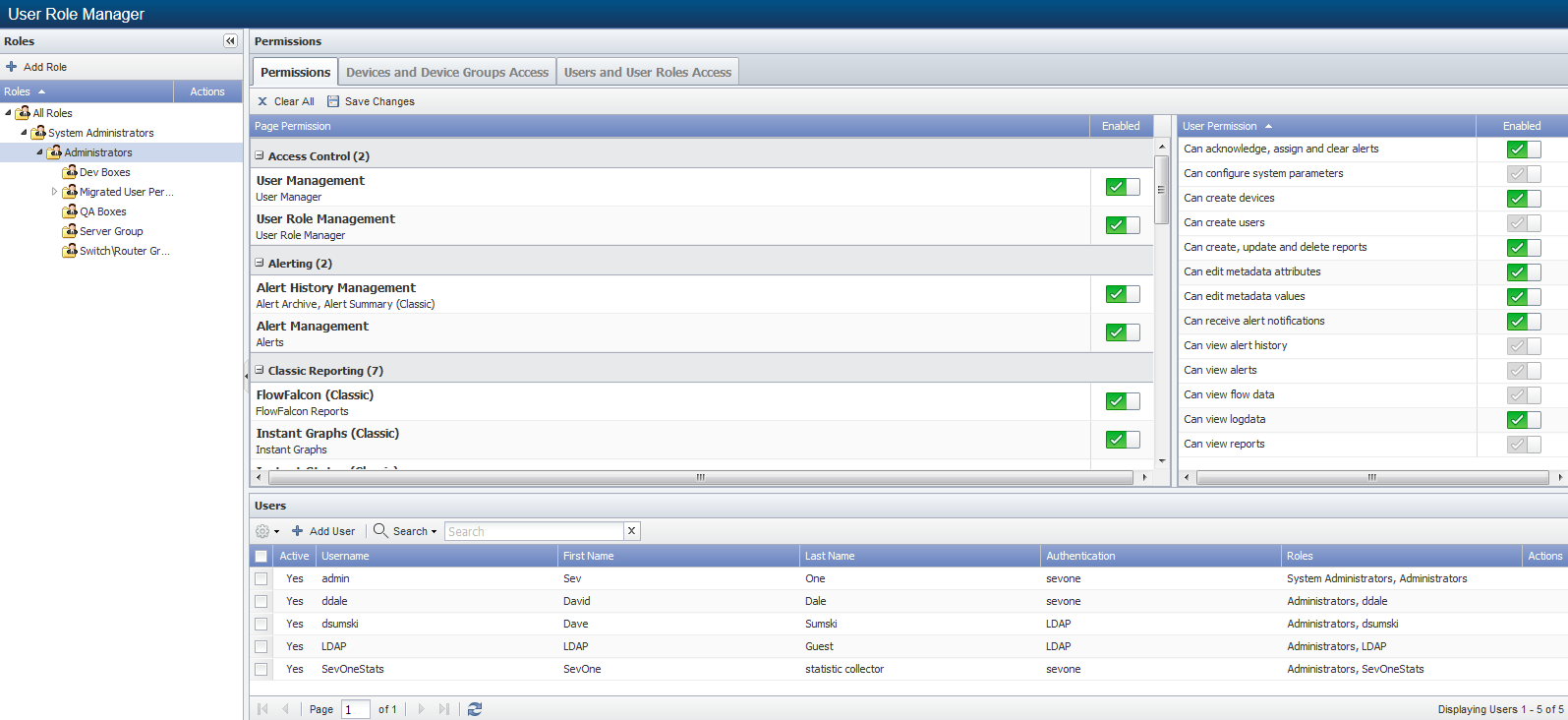
Manage Roles
The user roles to which you are granted Role View permission appear in the role hierarchy on the left side. The Users and User Roles Access tab enables you to define roles that have access to view roles but not edit roles that are above their role in the hierarchy.
-
Click Add Role or
 to display the Add/Edit Role pop-up.
to display the Add/Edit Role pop-up. -
For a new role, click the Parent drop-down and select the role under which to add the role in the role hierarchy. You cannot edit this field after you click Save.
-
In the Name field, enter the name of the role.
-
In the Description field, enter a description for the role.
-
Click Save.
Manage Permissions
The Permissions section provides three tabs to enable you to define the permissions for each role. All permissions are cumulative and each tab provides a subset of the permissions a user needs to perform tasks.
Example: To enable users to acknowledge, assign, and clear alerts, the user role must have;
-
Permissions tab -
-
Page Permission - Alert Management
-
User Permissions - Can Acknowledge, Assign, and Clear Alerts, and Can View Alerts
-
-
Devices and Device Groups Access tab - Enable access to device groups/device types that contain the devices from which the user is to be able to manage alerts.
-
Users and User Roles Access tab - Enable access to user roles that contain the users to which the user is to assign alerts.
As you enable permissions for higher level user roles, the same permission becomes available for the subordinate user roles. Conversely, when you disable permissions, the corresponding permissions are no longer available for the subordinate user roles.
The following buttons appear below the permissions tabs.
-
Click Clear All to reset the permissions on all tabs to their last saved settings.
-
Click Save Changes to save the changes made to all permissions on all tabs.
Page Permissions and User Permissions
The Permissions tab enables you to define which pages in SevOne NMS users assigned to the role can access and what the user can do on those pages. Additional Devices and Device Groups permissions and/or Users and User Roles permissions are required to actually see device data on the page. In other words, access to pages does not necessarily enable users to see or do anything on that page.
Page Permissions
The Page Permissions section enables you to grant users assigned to the role access to view applicable pages. As you enable page permissions, the corresponding minimum user permissions are enabled. You can enable additional user permissions when you feel they are applicable but you cannot disable the minimal user permission the page requires.
Example: You can grant a role the user permission Can Acknowledge, Assign, and Clear Alerts but if you do not enable the page permission to the Alerts page, the users in the role cannot see the workflows in the application that provide the ability to acknowledge, assign, or clear alerts.
Perform the following steps to manage the page permissions for a role.
-
In the Roles hierarchy, select a role to populate the Permissions tabs with the permissions for the role you select.
-
Select the Permissions tab, if needed.
-
In the Page Permission column, enable each permission to grant the users assigned to the role access to the pages listed.
When you disable all page permissions, an enabled user has permission to access the following pages.
-
Dashboard - (Administrative menu for these three pages only)
Access Control
-
Enable User Management to grant access to: User Manager.
-
Corresponding User Permissions: Can Create Users
-
-
Enable User Role Management to grant access to: User Role Manager.
-
Corresponding User Permissions: Can Create Users
-
Alerting
-
Enable Alert History Management to grant access to: Alert Archives and Alert Summary.
-
Corresponding User Permissions: Can View Alert History, Can View Alerts, Can View Reports
-
-
Enable Alert Management to grant access to: Alerts.
-
Corresponding User Permissions: Can View Alerts, Can View Reports
-
Classic Reporting
-
Enable FlowFalcon (classic) to grant access to FlowFalcon Reports.
-
Corresponding User Permissions: Can View Flow Data, Can View Reports
-
-
Enable Instant Graphs (classic) to grant access to: Instant Graphs.
-
Corresponding User Permissions: Can View Reports
-
-
Enable Instant Status (classic) to grant access to: Instant Status.
-
Corresponding User Permissions: Can View Alerts, Can View Reports
-
-
Enable NBAR Reporting (classic) to grant access to: NBAR Reports.
-
Corresponding User Permissions: Can View Reports
-
-
Enable Status Maps (classic) to grant access to: Status Map Manager.
-
Corresponding User Permissions: Can View Alerts, Can View Reports
-
-
Enable Telephony (classic) to grant access to: Telephony Browser and the Telephony Reports.
-
Corresponding User Permissions: Can View Reports
-
-
Enable TopN (classic) to grant access to: TopN Reports.
-
Corresponding User Permissions: Can View Reports
-
Device Management
-
Enable Device Manager to grant access to: Device Manager and SNMP Walk.
-
Corresponding User Permissions: None. You can enable the Can Create Devices user permission to grant users the ability to add devices. The Devices and Device Groups Access tab enables you to limit which devices users can see.
-
-
Enable Discovery Management to grant access to: Discovery Manager.
-
Corresponding User Permissions: None. You can enable the Can Create Devices user permission to grant users permission to add devices. The Devices and Device Groups Access tab enables you to limit which devices users can see.
-
-
Enable VMware Browser to grant access to: VMware Browser.
-
Corresponding User Permissions: None - Limits set from Devices and Device Groups Access tab
-
Metadata
-
Enable Metadata Attributes to grant access to: Metadata Schema.
-
Corresponding User Permissions: Requires Can Edit Metadata Attributes to edit the metadata attributes this page permission enables you to view.
-
-
Enable Metadata Values to grant access to Edit Metadata from the following pages: Device Types, Device Groups, Device Manager, Edit Device, Object Types, and Object Manager.
-
Corresponding User Permissions: Requires Can Edit Metadata Values to edit the values this page permission enables you to view.
-
Other
-
Enable Device Group Manager to grant access to: Device Groups.
-
Corresponding User Permissions: None - Limits set from Devices and Device Groups Access tab
-
-
Enable Object Manager to grant access to: Object Manager.
-
Corresponding User Permissions: None - Limits set from Devices and Device Groups Access tab
-
-
Enable Report Manager to grant access to: Report Attachment Wizard and Report Manager.
-
Corresponding User Permissions: Can View Reports
-
System Administration
-
Enable Cluster Configuration to grant access to: Authentication Settings, Baseline Manager, Cluster Manager, Device Mover, and Work Hours.
-
Corresponding User Permissions: Can Configure System Parameters
-
-
Enable Flow Monitoring Configuration to grant access to: Flow Interface Manager, Flow Rules, Flow Template Status, FlowFalcon View Editor, MPLS Flow Mapping, Network Segment Manager, Object Mapping, and Protocols and Services.
-
Corresponding User Permissions: Can Configure System Parameters
-
-
Enable Object Group Manager to grant access to: Object Groups.
-
Corresponding User Permissions: Can Configure System Parameters
-
-
Enable Polling Configuration to grant access to: Calculation Editor, Device Types, MIB Manager, Object Rules, Object Subtype Manager, Object Types, and SNMP OID Browser.
-
Corresponding User Permissions: Can Configure System Parameters
-
-
Enable Probe Provisioning to grant access to: Probe Manager and the Proxy Ping configuration on the Edit Device page.
-
Corresponding User Permissions: Can Configure System Parameters
-
-
Enable Threshold Configuration to grant access to: Policy Browser and Threshold Browser.
-
Corresponding User Permissions: none
-
-
Enable Trap Configuration to grant access to: Logged Traps, Trap Destinations, Trap Destination Associations, Trap Event Editor, Unknown Traps.
-
Corresponding User Permissions: Can Configure System Parameters
-
-
Enable xStats Configuration to grant access to: xStats Log Viewer, and xStats Source Manager.
-
Corresponding User Permissions: Can Configure System Parameters
-
User Permissions
The User Permission section enables you to grant additional permissions to users in the role. User permissions are governed by the Page Permission settings and the user is further limited by their Devices and Device Groups Access and their Users and User Roles Access.
-
Enable Can Acknowledge, Assign, and Clear Alerts to grant users assigned to the role permission to acknowledge, assign, and clear alerts when you also enable appropriate Devices and Device Groups permissions and you enable page permission for Alert Management.
-
Enable Can Configure System Parameters to grant users assigned to the role permission to perform system administration tasks when you also enable appropriate Devices and Device Groups permissions and you enable appropriate page permissions.
-
Enable Can Create Devices to grant users assigned to the role permission to create, edit, and delete device data when you also enable appropriate Devices and Device Groups permissions and you enable page permission for Device Manager.
-
Enable Can Create Users to grant users assigned to the role permission to create, edit, and delete user data when you also enable appropriate Users and User Roles permissions and you enable page permission for User Management and/or User Role Management.
-
Enable Can Create, Update, and Delete Reports to grant users assigned to the role permission to create and save report data when you also enable appropriate Devices and Device Groups permissions and you enable page permission for Instant Graphs, Device Manager, NBAR Reports, Report Manager, and/or Status Map Manager. Users assigned to the role can create disposable reports from these pages and can detach individual reports to a comprehensive report that they can save to the Report Manager.
-
Enable Can Edit Metadata Attributes to grant users assigned to the role permission to edit the metadata attributes on the Metadata Schema page.
-
Enable Can Edit Metadata Values to grant users assigned to the role permission to edit the values for the metadata attributes that are specific to a device type, device group, device, object group, or object.
-
Enable Can Receive Alert Notifications to grant users assigned to the role permission to receive email notifications from applicable traps, policies, and thresholds. This permission does not grant access to any workflows in SevOne NMS.
-
Enable Can View Alert History to grant users assigned to the role permission to view archived alerts when you also enable appropriate Devices and Device Groups permissions and you enable page permission for Alert History Management.
-
Enable Can View Alerts to grant users assigned to the role permission to view alerts when you also enable appropriate Devices and Device Groups permission and you enable the page permission for Alert Management.
-
Enable Can View Flow Data to grant users assigned to the role permission to view flow data in FlowFalcon reports when you also enable the appropriate Devices and Device Groups permission and you enable the page permission for FlowFalcon Reports.
-
Enable Can View Reports to grant users assigned to the role permission to view report data when you also enable appropriate Devices and Device Groups permissions and you enable page permission for Instant Graphs, Device Manager, NBAR Reports, Report Manager, and/or Status Map Manager. Users assigned to the role can create disposable reports from these pages and can detach individual reports to a comprehensive report but they cannot save reports to the Report Manager.
Devices and Device Groups Access
The Devices and Device Groups Access tab enables you to grant users assigned to the role permissions to view and/or edit specific device groups/device types and/or to view and/or edit specific devices.
-
Select the Devices and Device Groups Access tab.
-
Enable the following to grant users you assign to the role permission to view and/or edit device groups/device types and the devices within device groups/device types.
As you enable the Devices and Device Groups permissions for higher level user roles, the same Devices and Device Groups permissions becomes available for the subordinate user roles. Conversely, when you disable the Devices and Device Groups permissions, the corresponding Devices and Device Groups permissions are no longer available for the subordinate user roles.
-
Enable Group View to grant users assigned to the role permission to view the name of the device group/device type. Users cannot see the devices that are members of the device group/device type or any corresponding device data until you enable Device View permission.
-
Enable Group Edit to grant users assigned to the role permission to edit the device group/device type name. Enable Device View permissions to grant permission to edit the list of devices that are members of the device group/device type.
-
Enable Device View to grant users assigned to the role permission to see the devices that are members of the device group/device type and applicable corresponding device data. If you disable the Group View permission, users assigned to the role can see the devices that are members of the device group/device type but cannot see the device group/device type name.
-
Enable Device Edit to grant users assigned to the role permission to edit the configuration of the devices that are members of the device group/device type.
-
Users and User Roles Access
The Users and User Roles Access tab enables you to define which user roles users assigned to the role can see and/or edit and which users the users assigned to the role can see and/or edit.
-
Select the Users and User Roles Access tab.
-
Enable the following permissions to grant users assigned to the role permission to view and/or edit user roles and the users assigned to the user roles.
As you enable the Users and User Roles permissions for higher level user roles, the same Users and User Roles permissions become available for the subordinate user roles. Conversely, when you disable the Users and User Roles permissions, the corresponding Users and User Roles permissions are no longer available for the subordinate user roles.
-
Enable Role View to grant users assigned to the role permission to view the name of the user role. Users assigned to the role cannot see users assigned to the user role until you enable applicable User View permissions.
-
Enable Role Edit to grant users assigned to the role permission to edit the user role name. Enable applicable User View permissions to grant users assigned to the role permission to manage the user assignments for the role.
-
Enable User View to grant users assigned to the role permission to view the users in the role.
-
Enable User Edit to grant users assigned to the role permission to edit the user information, credentials, and role assignments for the users who are assigned to the user role.
-
Manage Users
The Users section enables you to manage users and user role assignments. Users can update their first name, last name, email address, and password from the Preferences page.
-
Select the check box for each user to manage, click
 , and select Enable, Disable, or Delete to enable, disable, or delete the users you select.
, and select Enable, Disable, or Delete to enable, disable, or delete the users you select. -
Click Add User or
 to display the Add/Edit User pop-up that enables you to manage the user information, credentials, and role assignments.
to display the Add/Edit User pop-up that enables you to manage the user information, credentials, and role assignments. -
In the User Information section, in the First Name field, enter the first name to appear wherever a user name appears.
-
In the Last Name field, enter the last name to appear wherever a user name appears.
-
In the Email field, enter the email address where you want SevOne NMS to send emails to the user.
-
In the Credentials section, in the Username field, enter the name for the user to enter into the Username field on the Login page. You cannot edit this field after you click Save.
-
Click the Authentication drop-down and select the method for the user to use when they log on. Select the SevOne authentication unless your company uses LDAP, RADIUS, or TACACS protocol to authenticate users.
-
In the Password field, enter the user password. This field and the Confirm field are not applicable for users who use TACACS, LDAP, or RADIUS because password management for these protocols is done through the corresponding authentication servers.
-
In the Confirm field, re-enter the user password.
-
Click the Role Assignments drop-down and select the user roles to which to assign the user. You can assign users to multiple roles and role permissions are cumulative.
-
Select the User Enabled check box to enable the user to log on and use SevOne NMS. Clear this check box to block access to the user without having to delete the account.
-
Select the The Password for This User Will Never Expire check box to override the Maximum Password Age setting you define on the Cluster Manager Cluster Settings tab. This check box does not appear when you do not enable the Maximum Password Age setting on the Cluster Manager.
-
Select the Force Password Change Upon Next Login check box to force the user to change the password when they log on for the first time.
-
Select the Custom Timeout check box to enable the user to stay logged on during periods of inactivity for the amount of minutes you enter in the Custom Timeout field. Leave clear to have the user log off after the amount of time you enter on the Cluster Manager. This setting overrides the Inactivity Timeout setting you enter on the Cluster Manager Cluster Settings tab. The user must log out and then log back on for this setting to take effect.