Table of Contents (Start)
SevOne NMS 5.4 Quick Start Guide - LDAP
SevOne NMS Documentation
All SevOne NMS user documentation is available online from the SevOne Support website.
-
Enter email address and password.
-
Click Login.
-
Scroll down to the Solutions section.
© Copyright 2015, SevOne Inc. All rights reserved. SevOne, SevOne PAS, SevOne DNC, Deep Flow Inspection, and Rethink Performance are either registered trademarks or trademarks of SevOne Inc. Other brands, product, service and company names mentioned herein are for identification purposes only and may be trademarks of their respective owners.
Introduction
This document describes the best practices for SevOne NMS users to implement and manage authentication using Lightweight Directory Access Protocol (LDAP). LDAP is an application protocol to query and modify directory services that run over TCP/IP to authenticate onto SevOne NMS.
SevOne NMS supports LDAP authentication for individual users and LDAP group synchronization for Active Directory and OpenSSL.
SevOne NMS provides an Authentication Settings page to enable you to configure authentication into SevOne NMS via LDAP.
To access the Authentication Settings page from the navigation bar, click the Administration menu, select Access Configuration, and then select Authentication Settings.
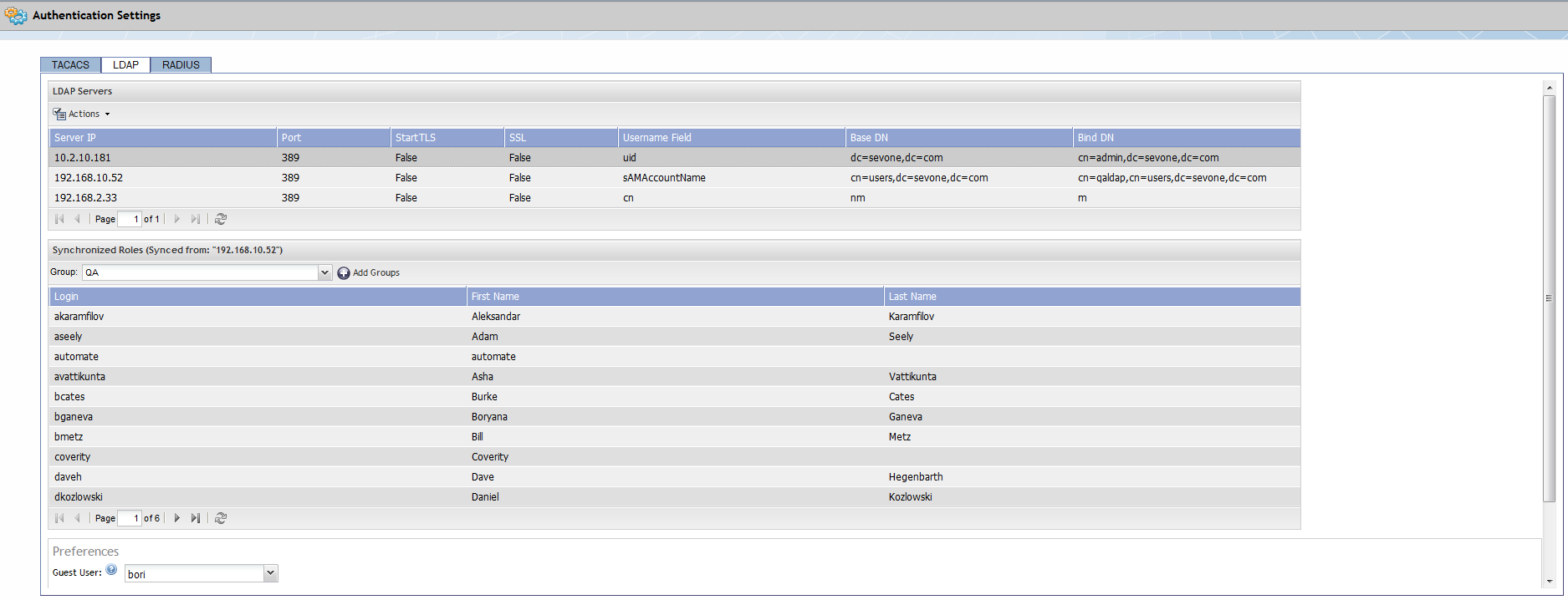
Manage LDAP Servers in SevOne NMS
The Authentication Settings page - LDAP tab enables you to configure communication with the LDAP protocol authentication server.
 - The Actions icon enables you to add and manage the LDAP servers in SevOne NMS.
- The Actions icon enables you to add and manage the LDAP servers in SevOne NMS.
-
New Server – Select to add an LDAP server to SevOne NMS.
-
Edit Server - Select to edit the LDAP server you select.
-
Test Settings - Select to test the connection to the LDAP server.
-
Delete Server - Select to delete the LDAP server you select.
Add/Edit LDAP Servers to SevOne NMS
Perform the following steps to add or edit the LDAP server settings that SevOne NMS uses to authenticate users.
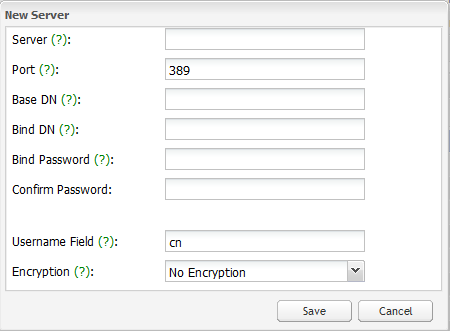
-
 Actions - Click and select New Server to display the New Server pop-up.
Actions - Click and select New Server to display the New Server pop-up. -
In the Server field, enter the host name or IP address of the LDAP server.
-
In the Port field, enter the network port of the LDAP server. The default LDAP port is 389. The default LDAPS port is 636 which has been deprecated.
-
In the Base DN field, enter the base distinguished name (DN) on which to do LDAP queries. The top level of the LDAP directory tree is the base, referred to as the base DN from which a search starts. For an Active Directory system this is typically dc=example, dc=com.
-
In the Bind DN field, enter the user name to which SevOne NMS is to authenticate and whose authorizations SevOne NMS is to use to search the tree. The BIND operation establishes the authentication state for a session.
Example: cn=guest.
-
In the Bind Password field, enter the password for the user name you enter in the previous step. This is not required in LDAP version 3 (LDAPv3).
-
In the Confirm Password field, reenter the bind password.
-
In the Username Field field, enter the LDAP field SevOne NMS is to check to find user names. In Active Directory, this is typically sAMAccountName. Many other directories use cn.
-
Click the Encryption drop-down.
-
Select No Encryption to not use encryption.
-
Select StartTLS to use StartTLS. StartTLS secures the LDAP credentials and data. Start TLS is sometimes referred to as the TLS upgrade operation because it upgrades a normal LDAP connection to a connection that is protected by TLS/SSL.
-
Select SSL (LDAPS, dep) to use Secure Socket Layers (SSL). SSL secures LDAP data. A method to secure LDAP communication is to use an SSL tunnel. This is denoted in LDAP URLs by using the URL scheme "ldaps". The use of LDAP over SSL was common in LDAPv2. This usage has been deprecated along with LDAPv2.
-
-
Click Save.
Synchronize Roles/Groups
The Synchronized Roles section enables you to associate the LDAP server groups on the LDAP server to the User Roles in SevOne NMS. This document assumes knowledge of how to create LDAP groups on the LDAP server and assumes knowledge of how to create user roles on the User Role Manager in SevOne NMS.
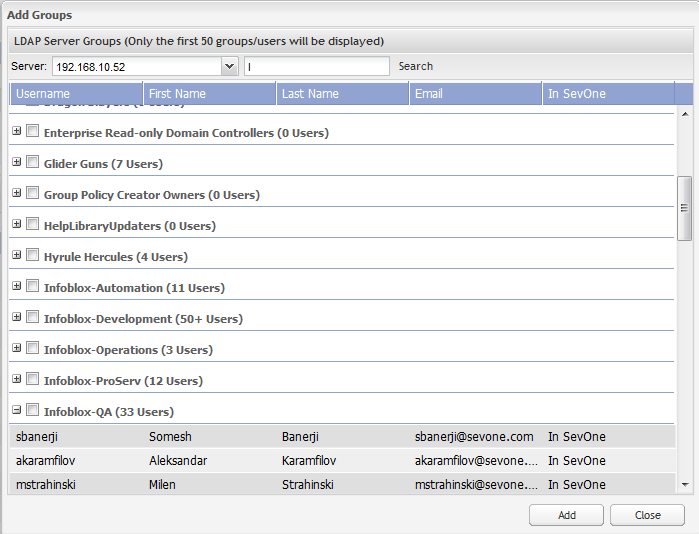
-
Click the Group drop-down and select the group to which to associate the server you select.
-
If the group you are looking for does not appear, click Add Groups to display the Add Groups pop-up.
-
Click the Server drop-down and select a server.
-
In the Search field, enter at least one letter to filter the search results and press Enter.
-
In the list of groups, click the + next to the group name to display the group members.
-
Select the check box for each group to add.
-
Click Add to add the groups you select.
Preferences
The Preferences section enables you to define the guest user and to manage the LDAP certificates.
-
Click the Guest User drop-down and select the guest user to provide permissions for anyone who logs on with a valid LDAP ID but no SevOne NMS account.
-
Next to the SSL/TLS Certificates caption, click Upload New to display the Upload SSL/TLS CA Root Certifications pop-up. You must upload the CA Root Certificates to enable SevOne NMS to communicate with an LDAP server that has certificates that are signed by an unknown CA.
-
Click Browse to locate and select the certificate. The certificates must be base64-encoded PEM files.
-
Click Upload to upload the certificate.
-
Select the Ignore SSL/TLS Certificates check box to ignore the certificates (not recommended).
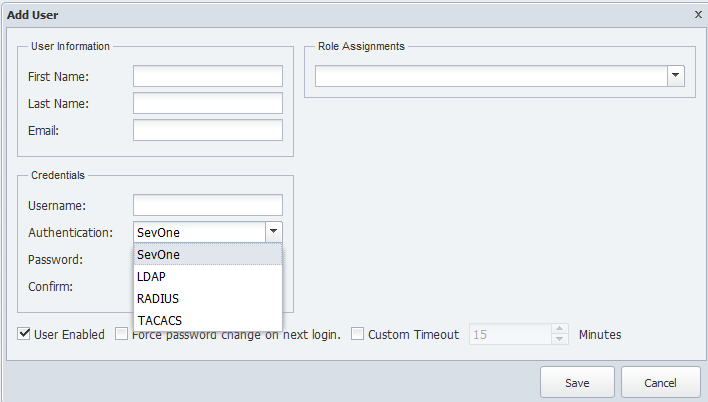
User Manager
The LDAP server populates the SevOne NMS User Manager with the applicable users.
Each SevOne NMS user has the LDAP Authentication credentials and can be added to additional SevOne NMS role assignments on the User Manager.