
Table of Contents (Start)
Enable WMI
This documentation applies to NMS version 5.4. An online version of the software can be found here.
The WMI plugin polls WMI data such as: CPU usage, ASP.NET, hard drive usage, and memory usage monitors. WMI data appears throughout the application in Instant Graphs, TopN Reports, thresholds, and other workflows. You can mix match WMI and SNMP to create logical thresholds. This topic describes workflows outside of the SevOne NMS application and may not present all of the steps your network requires to enable devices to send WMI data. If the following instructions are not applicable for your network please reference the device manufacturer's documentation.
There are several steps to set up your network to enable SevOne NMS to monitor WMI data from devices for which you enable the WMI plugin.
A) Set up the WMI proxy server to communicate with SevOne NMS (this chapter).
B) Set up your network's Windows devices to communicate with the WMI proxy server (this chapter).
C) Set up the WMI plugin for each WMI device from the New Device page and the Edit Device page.
D) Enable the WMI object types for the WMI plugin to poll from the Object Types page.
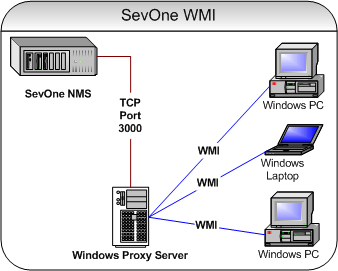
Set Up WMI Proxy Servers
The first step to set up SevOne NMS to monitor WMI data is to create a WMI proxy server. SevOne NMS provides a Windows service for you to install on the Windows machine that you want to act as the proxy server to perform WMI queries. The WMI Proxies subtab on the Cluster Manager Cluster Settings tab enables you to add, edit, and delete the WMI proxies for SevOne NMS to use.
-
In SevOne NMS, click the Administration menu and select Cluster Manager to display the Cluster Manager.
-
At the cluster level, select the Cluster Settings tab.
-
Select the WMI Proxies subtab.
-
Click the WMI Proxy Download Installation Package link and save the file to the proxy server.
-
If the proxy server is not running the Microsoft .NET 3.5 framework, click the .NET 3.5 Framework Download Installation Package link and save the file to the proxy server.
-
On the proxy server, run the .NET 3.5 Framework setup.exe, if needed, and then run the SevOne NMS WMI Proxy Setup.msi.
-
Click Start and select Control Panel.
-
Double-click Administrative Tools.
-
Double-click Component Services.
-
Double-click Services (Local).
-
Right-click on SevOne NMS WMI Proxy and select Start.
-
On the proxy server, ensure that the user account is the local administrator.
-
In SevOne NMS, on the Cluster Manager WMI Proxies subtab, click Add WMI Proxy to display the Add WMI Proxy pop-up.
-
On the Add WMI Proxy pop-up, in the Name field, enter the name of the proxy server.
-
In the IP Address field, enter the proxy server IP address.
-
In the Port field, enter the port for the proxy server to use to communicate with SevOne NMS (default - 3000).
-
Click Save on the Add WMI Proxy pop-up.
-
Repeat the previous steps to define additional WMI proxy servers.
-
Click Save on the WMI Proxies subtab to save the WMI Proxy cluster settings.
Set Up Windows Devices
This section describes how to enable WMI, allow remote administration, and enable the Windows device to communicate back to the WMI proxy on each Windows device from which you want to poll WMI data. WMI must establish a DCOM connection from Computer A (the SevOne NMS WMI proxy server) to Computer B (the remote computer). The following diagram shows this as Connection 1. To establish this connection, configure both the Windows Firewall and DCOM on Computer B. The configuration must be done locally on Computer B because Windows Firewall does not support remote configuration. Either execute NETSH commands to change the Group Policy settings or execute a script locally.
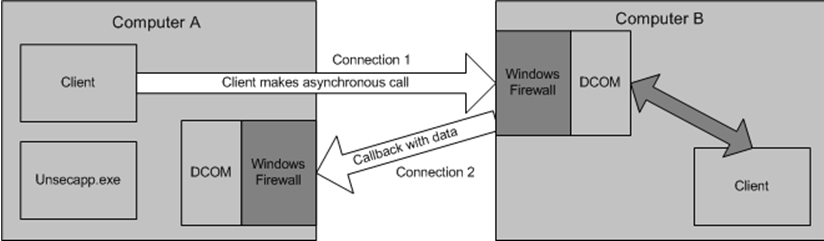
Computer A is the WMI Proxy Server for SevOne NMS
Computer B represents each of your network's Windows devices
Enable WMI
Perform the following steps on each Windows device to start the WMI service.
-
Click Start and select Control Panel.
-
Double-click Administration Tools.
-
Double-click Services.
-
Scroll down to WMI Performance Adapter, right-click WMI Performance Adapter and select Start.
-
Right-click WMI Performance Adapter and select Properties.
-
Select the General tab.
-
Click the Startup Type drop-down and select Automatic to have the service start every time the computer starts.
-
Continue to the next section to allow remote administration on each Windows device (create Connection 1 in the diagram).
Allow Remote Administration
On each Windows device, enable Allow Remote Administration to allow the Windows device to accept the communication from the WMI proxy server.
You can enter one of the following commands.
For Windows 7+ enter: netsh advfirewall firewall set rule group="Windows Remote Management" new enable=yes
For Windows older than 7 enter: Netsh firewall set service RemoteAdmin enable
Or you can perform the following steps.
-
Click Start and select Run.
-
In the Open field, enter gpedit.msc and click OK to display the Group Policy page.
-
On the right side in the Local Computer Policy section, double-click Computer Configuration.
-
Double-click Administrative Templates.
-
Double-click Network.
-
Double-click Network Connections.
-
Double-click Window Firewall.
-
Perform one of the following steps:
-
If the computer is in the domain, double-click Domain Profile.
-
If the computer is not in the domain, double-click Standard Profile.
-
-
Right-click on Windows Firewall: Allow Remote Administration Exception and select Properties.
-
Select the Enabled option.
-
Click OK.
-
Click X to close the Group Policy page.
-
Continue to the next section to allow the Windows device to communicate with the WMI proxy server.
Enable Windows Devices to Communicate Back
The connection from Computer B to Computer A (Connection 2 in the diagram) is only required when the client script or application makes an asynchronous call to the remote computer. If Computer B is either a member of Workgroup or is in a different domain that is not trusted by Computer A, then Connection 2 is created as an Anonymous connection.
-
If the Windows Firewall is enabled on Computer A, run the following command on Computer A to enable Allow Remote Administration exception and to open DCOM port TCP 135 on Computer A.
netsh firewall add portopening protocol=tcp port=135 name=DCOM_TCP135 -
Add the client application script, which contains sink for the callback to the Windows Firewall Exception List on Computer A. If the client is a script or a MMC snap-in, the sink is often Unsecapp.exe. For these connections, add %windir%\system32\wbem\unsecapp.exe to the Windows Firewall application exception list.
netsh firewall add allowedprogram program=%windir%\system32\wbem\unsecapp.exe name=UNSECAPP
WMI Plugin and WMI Object Types
After you perform all of the steps in this topic for all Windows devices for which to monitor WMI data, turn on the WMI plugin for each device from the Edit Device page and enable the WMI object types for the WMI plugin to poll on the Object Types page.